Enterprise data security best practices in 2025 help you keep important information safe. They also lower risks from cyber threats. You face more dangers now, like credential harvesting and data theft. Reports say 166 million people had their data compromised in the first half of 2025.
| Statistic Description | Value | Year |
|---|---|---|
| Individuals affected by data compromises | 166 million | H1 2025 |
| Average cost of data breach | $4.44 million | 2025 |
You should check your security often. Platforms like FineDataLink by FanRuan, FineReport, and FineBI have helpful features. These include encryption and secure transmission. These tools help you follow rules and keep your data protected.
Data is important for your business. Enterprise data security keeps your information safe from loss or theft. There are more risks now than before. Your data is stored in many places. It can be in the cloud, on devices, or in different systems. This makes it harder to protect everything.
Insider threats are a big problem. People inside your company might leak data. Sometimes it is by accident. Sometimes it is on purpose. You need strong rules to stop this. Modern tools help you find problems fast. Machine learning can sort data and warn you about risks.
FanRuan wants to help you use data safely. You can make smart choices when your data is protected. FineDataLink lets you manage and guard your data everywhere. This helps you stay safe from new dangers. It also helps you follow privacy rules.
Note: Enterprise data security is more than stopping hackers. It helps you build trust with customers and partners. Protecting data keeps your reputation safe.
Threats change all the time. You need to watch for new dangers every day. Attackers use smart ways to steal data or hurt your business. Hackers from outside are a risk. People inside your company can also cause problems.
Here are some ways enterprise data security has changed:
Reports show each industry has its own problems. The table below shows important trends and threats for 2025:
| Sector | Key Trends and Challenges |
|---|---|
| Healthcare | Strong endpoint encryption, zero trust, following HIPAA and privacy laws. |
| Financial Services | Better monitoring, AI to find problems, checking transactions, MFA, device trust, micro-segmentation. |
| Retail and E-Commerce | Using DevSecOps, WAF solutions, following PCI DSS, stopping fraud fast. |
| Government and Public Sector | Zero trust, watching endpoints, training staff, working with private security companies. |
| Manufacturing and Industrial IoT | Special OT security software, patching often, network micro-segmentation, strong endpoint checks. |
You need to stay alert and update your defenses often. Enterprise data security gives you what you need to keep your business safe.
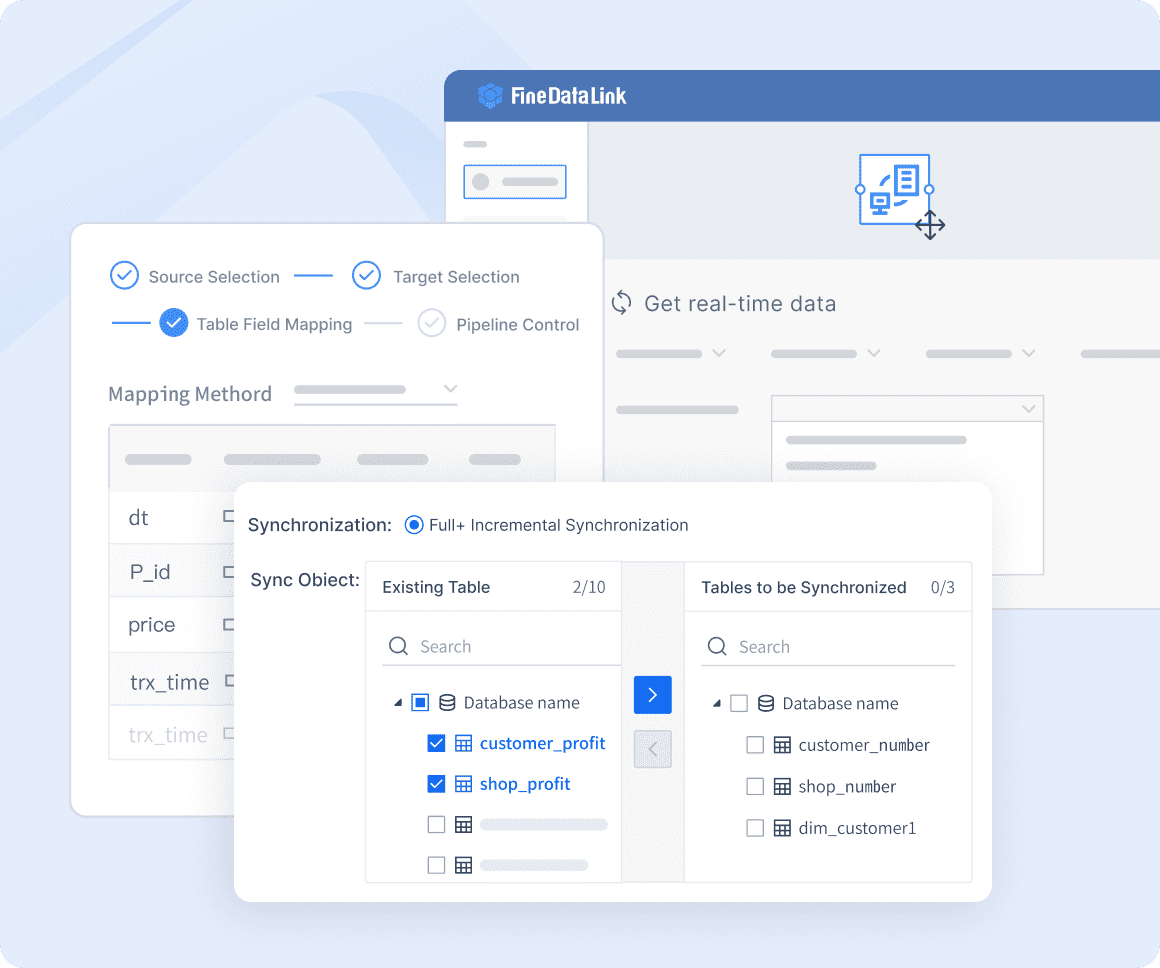
You must know where your sensitive data is. Data identification helps you find and label important information. This step is important for risk management and following rules like GDPR. You make a list to keep track of your data.
FineDataLink helps you sort and find data from many places. You see your information clearly, so it is easier to keep safe.
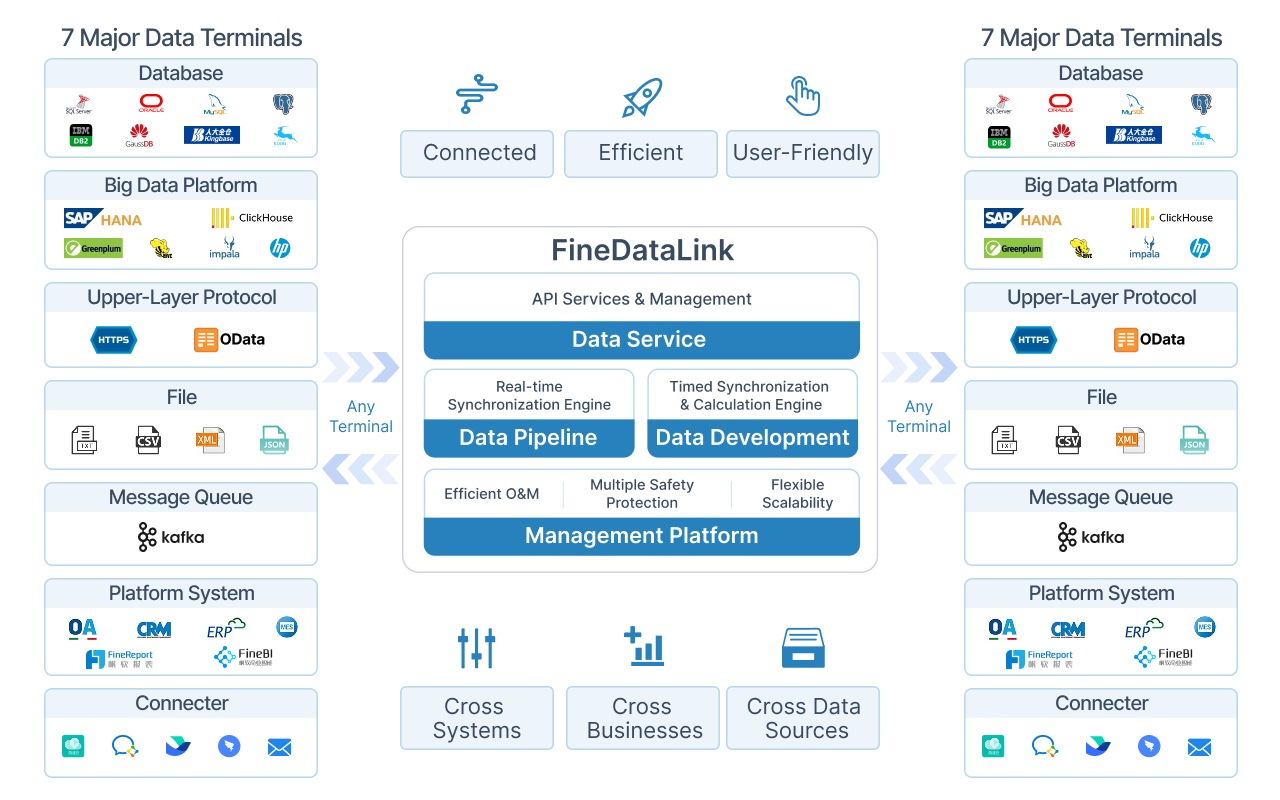
Access controls help you choose who can see or use your data. You set strong rules to keep out people who should not get in. You lower the chance of leaks or theft. You use least privilege rules so users only get what they need.
Studies show access controls stop people from getting in without permission. You keep your data safe by letting only trusted users reach it.
Encryption changes your data into secret code. Only people with the right key can read it. New methods like homomorphic encryption let you use encrypted data without unlocking it. Honey encryption makes it harder for attackers to guess your secrets. End-to-end encryption keeps your data safe from start to finish, which is good for remote work.
FineDataLink helps you change data safely. You can use encryption to protect data as it moves between systems.
Monitoring is an important part of enterprise data security. You watch your systems all the time. You look for strange activity and signs of danger. Continuous monitoring helps you act fast if something goes wrong.
Monitoring for threats means you always know what is happening. FineDataLink keeps your data updated and correct, which helps with monitoring. You get automatic alerts and reports, so you can find problems quickly.
| Feature | Description |
|---|---|
| Data Integration from Multiple Sources | Brings together data from different places, so you can see everything. |
| Data Consistency | Makes sure data from different places matches, so there are fewer mistakes. |
| Automated Data Synchronization | Updates reports and dashboards with new information automatically. |
| Seamless Data Transformation | Changes data during integration, so it is ready for analysis. |
Tip: You should use monitoring tools to keep your enterprise data security strong. Regular checks help you find and fix problems fast.
You should use the Zero Trust Model to keep your business safe. This model means you do not trust anyone right away. You always check every request before letting someone in. You give users only what they need to do their job. You look at the situation and risk before giving access. You watch what people do all the time and change rules if you see trouble. You do not use public IP addresses so attackers cannot get in.
| Principle | Description |
|---|---|
| Never Trust, Always Verify | You check every request using many things. |
| Least-Privileged Access | You give users only what they need for work. |
| Contextual and Risk-Based Access | You use AI and machine learning to check risk for each request. |
| Continuous Monitoring | You watch for risks and change rules when needed. |
| No Public IP Addresses | You hide apps from public networks to lower risk. |
FineDataLink helps you use these security steps. You can control who gets in, watch what happens, and keep your data safe everywhere.
Tip: Always check users and devices before letting them in. This helps stop breaches.
You should use multi-factor authentication (MFA) in your security plan. MFA asks users for more than one proof of who they are. This makes it much harder for attackers to break in. Many attacks happen when someone steals a password. MFA can stop almost all of these attacks.
FineDataLink uses MFA for safe data integration. You can use MFA to protect your data pipelines and APIs.
You need strong password rules to keep your data safe. You should use a password manager to help workers make and save strong passwords. You should not make people change passwords too often, because this can lead to weak choices. You should lock accounts after too many wrong tries.
New password rules focus on changing passwords after a problem. You should update passwords after a security issue, not just by time.
FineDataLink helps you set password rules for everyone. You can make rules for strong passwords and watch for risky actions.
You must update your software often. Updates fix problems and close security holes. Hackers look for old software with known weaknesses. Groups like Volt Typhoon attack outdated systems. You keep your business safe by installing updates quickly.
FineDataLink makes it easy to keep your tools updated. You get alerts for new versions and can add patches with simple steps.
You should use automated data classification to organize your information. This helps you protect sensitive data and follow privacy laws. Automated tools sort data by type and risk level. You save time and avoid mistakes.
| Benefit | Description |
|---|---|
| Improved Data Protection | You protect sensitive data with better security rules. |
| Compliance with Regulations | You meet legal standards and prepare for audits. |
| Operational Efficiency | You manage data faster and with fewer errors. |
FineDataLink uses automated data classification. You can label data from many places and set rules for each type. This is one of the best ways to keep data safe in big companies.
You need strong data loss prevention steps. You should sort and label sensitive data. You should limit access based on user roles. You should watch what users do in real time. You should teach workers how to handle data safely. You should check and improve your rules often.
FineDataLink helps you set up data loss prevention by tracking data movement and access. You can use its tools to spot risks and stop leaks before they happen.
Alert: Data loss prevention is very important for keeping your business safe. You should use automated tools to catch problems early.
You must keep restore-able backups of your data. Backups help you get your data back after mistakes, system failures, or cyberattacks. If ransomware hits, you can restore your data without paying. This keeps your business running and protects your reputation.
FineDataLink helps with backup and recovery. You can set up backups and restore data fast. Every company should use this data security step.
You should protect your data centers with strong physical security. You need perimeter detection, video cameras, and AI analytics. You should use biometric access controls and layer your security steps.
"Data centers are the banks of the currency of the 21st century, and that currency is data. It needs to be guarded all the time with different tools and tactics." — Sean Farney, VP, Data Center Strategy, JLL
FineDataLink works with secure places. You can use it in data centers with strong physical security to keep your information safe.
Note: You should use these best steps for keeping data safe to build a strong defense. FineDataLink helps you follow these steps with secure, real-time data integration and compliance support.
You can keep your business safe with real-time data integration. FineDataLink connects data from many places and updates it right away. This helps you find threats like ransomware and phishing before they hurt you. You use encryption to protect your data as it moves. You also use identity and access management tools, like single sign-on and multi-factor authentication, so only trusted users get in.
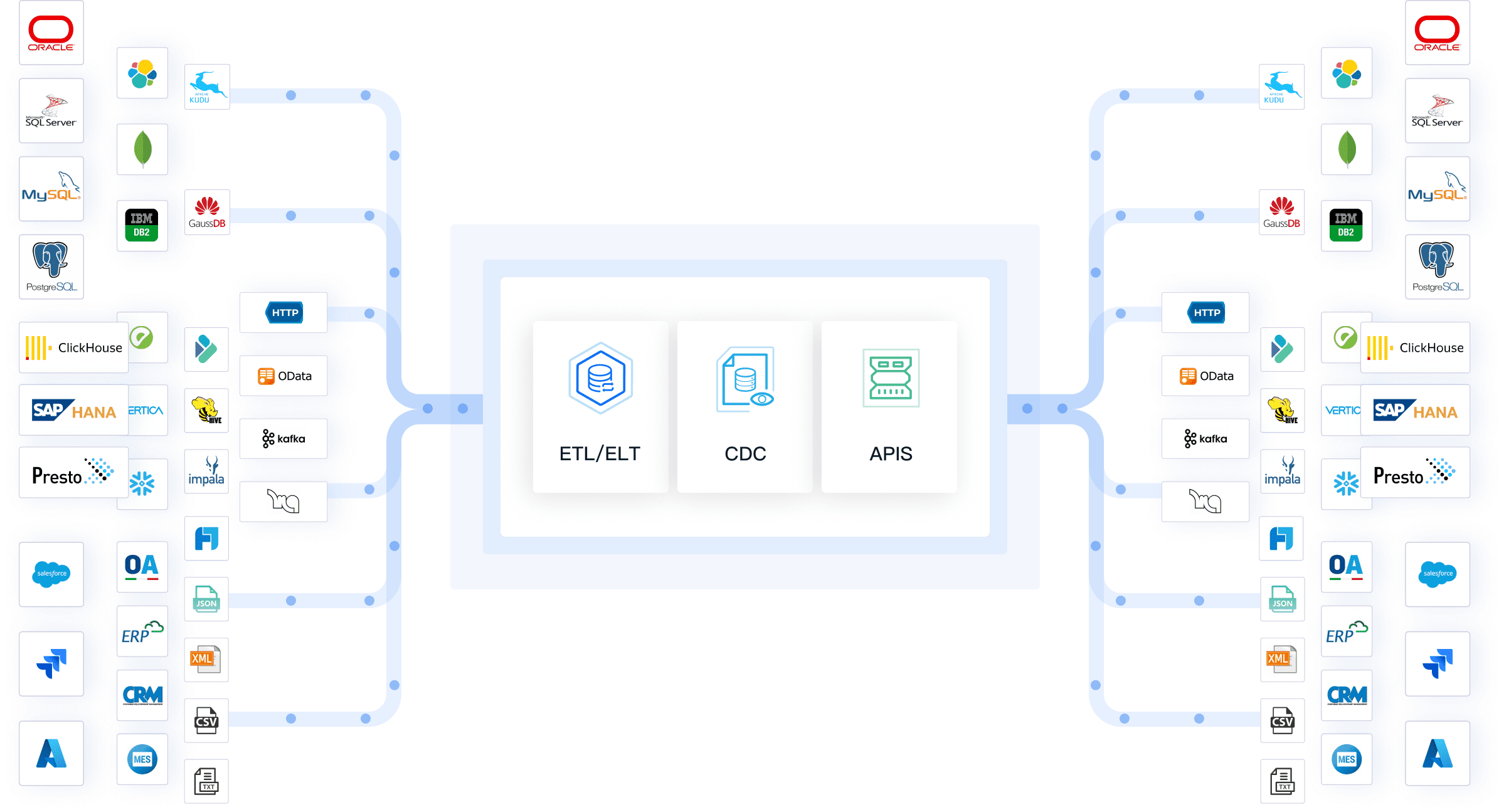
Benefits of Real-Time Data Integration:
Tip: Real-time integration lets you act fast when risks show up and keeps your data safe everywhere.
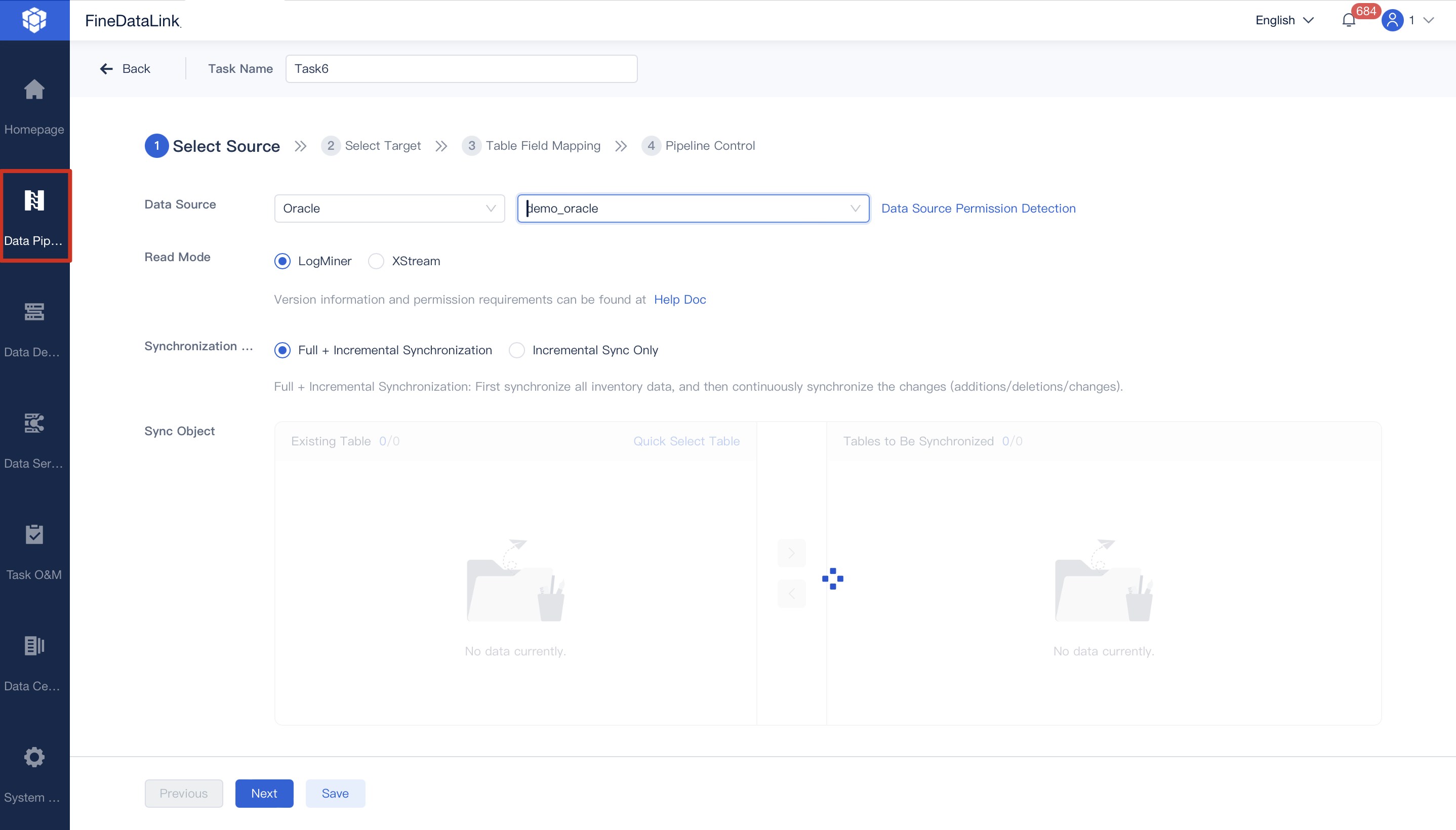
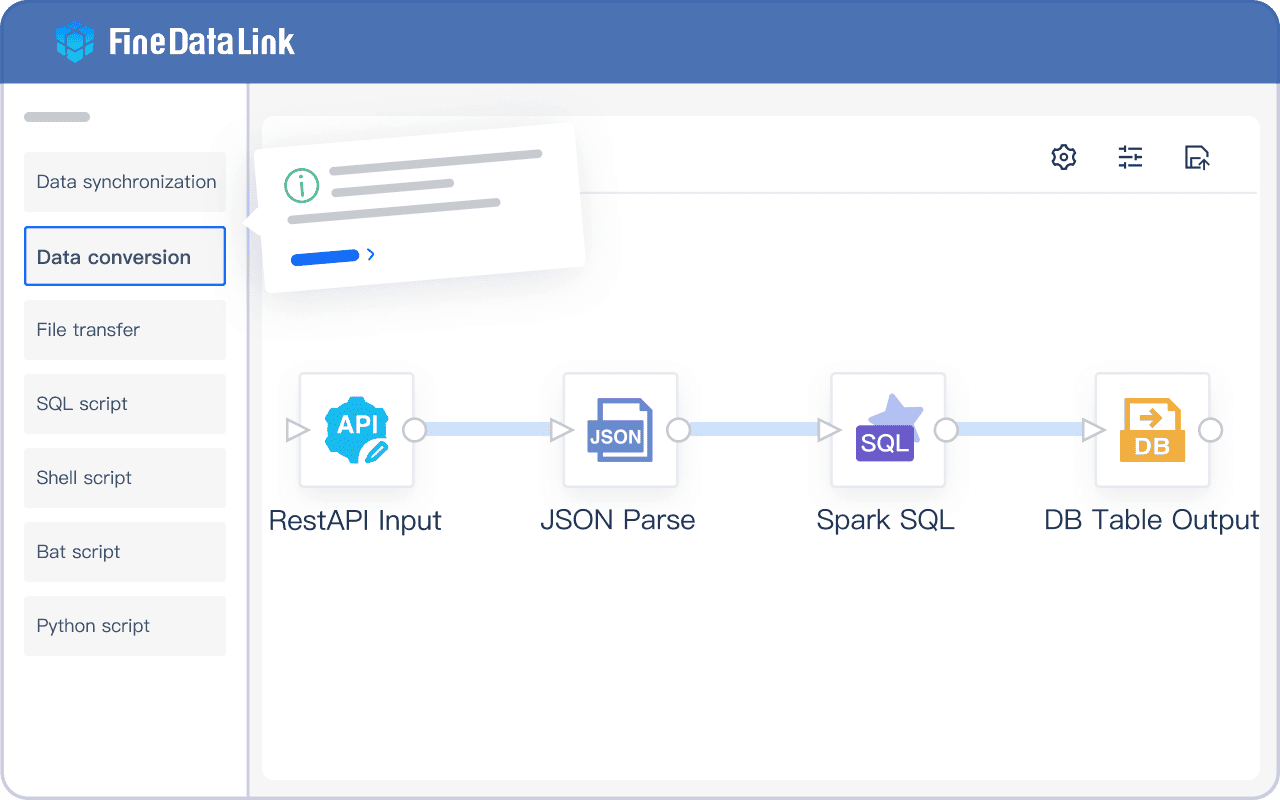
FineDataLink works with both ETL and ELT. You use ETL to clean and check data before putting it in your warehouse. This makes sure your data is good and safe. You use ELT when you change data after loading it. You need strong data quality tools in your warehouse for ELT to work well.
| Aspect | Description |
|---|---|
| Access Control | You pick who can read or change data. |
| Data Storage Rules | You set rules to store data safely. |
| Data Retention | You choose how long to keep each type of data. |
| Security Policies | You use rules to protect stored data and lower risks. |
| Pre-load Transformations | You hide or encrypt sensitive data before loading it. |
You fix problems like data silos and manual work by using FineDataLink’s ETL/ELT features.
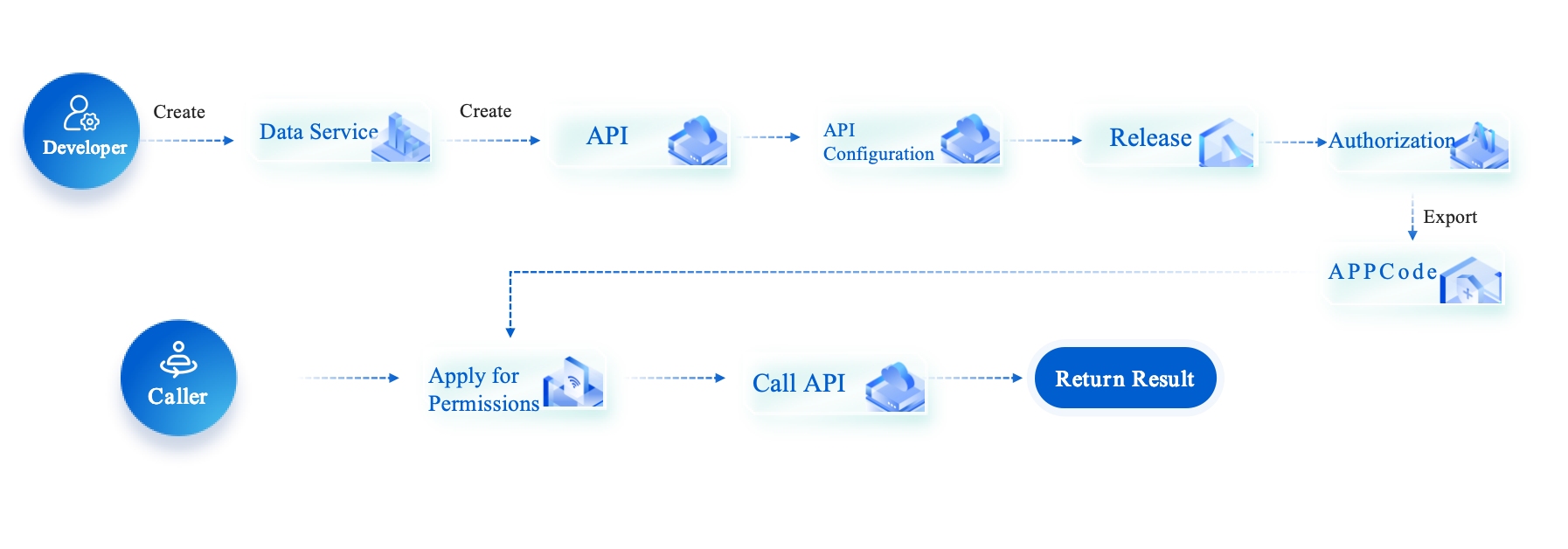
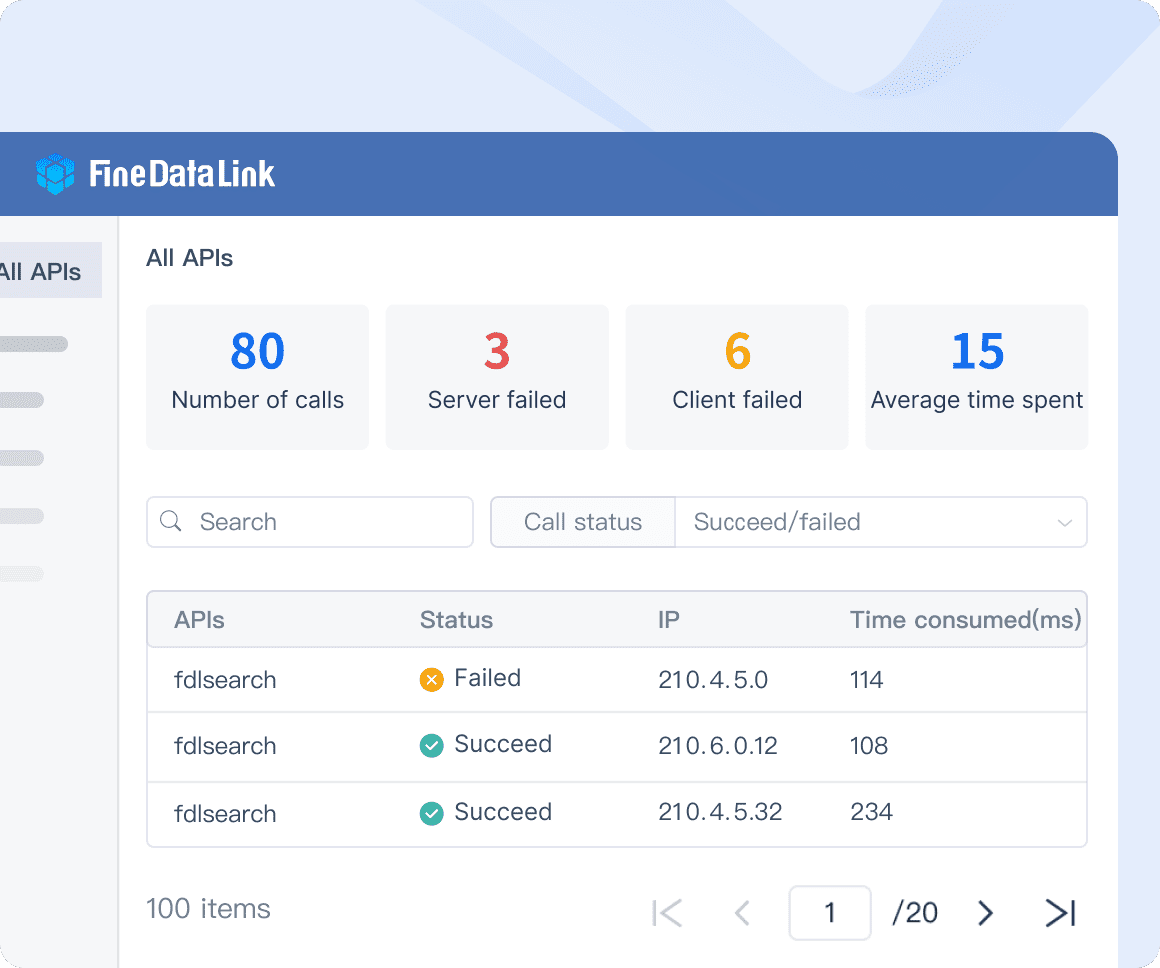
You use APIs to share data between systems. You must keep your APIs safe from common dangers. FineDataLink helps you set strong rules for authentication and authorization. You check what goes in and out to stop attacks like injection and broken access control. You set limits so systems do not get overloaded.
You lower these risks by using FineDataLink’s secure API tools. You can start APIs quickly and safely, even if you do not code.
You need strong data governance to keep your information safe. FineDataLink helps you make clear rules and roles. You make sure only the right people can use or change data. You follow laws like GDPR and HIPAA by using good processes.
Data governance sets rules and roles that help you keep data safe, correct, and easy to use. This is important for smart choices and following privacy laws.
You make your data better and build trust by using FineDataLink’s governance features. You fix problems like hard data formats and manual work.
| Category | Best Practices |
|---|---|
| Application Security | Use encryption, check uploads, protect web apps. |
| Account Security | Use single sign-on, last login checks, access control, strong passwords. |
| Data Security | Control who can see data, encrypt storage, use watermarks for reports. |
| Operation & Maintenance | Check operations, back up systems often. |
| Mobile App Security | Make identity, data, and network security stronger in mobile apps. |
Note: FanRuan solutions like FineDataLink help you build a safe, smart, and legal data system for your company.

You need a strong tool to keep your data safe. FineDataLink lets you connect data from many places. It works in real time and uses ETL/ELT and secure APIs. You can link over 100 data sources. Your data stays safe as it moves between systems. FineDataLink is easy to use because it has a visual interface. You do not have to write code to set up data pipelines or APIs. This saves you time and helps you make fewer mistakes.
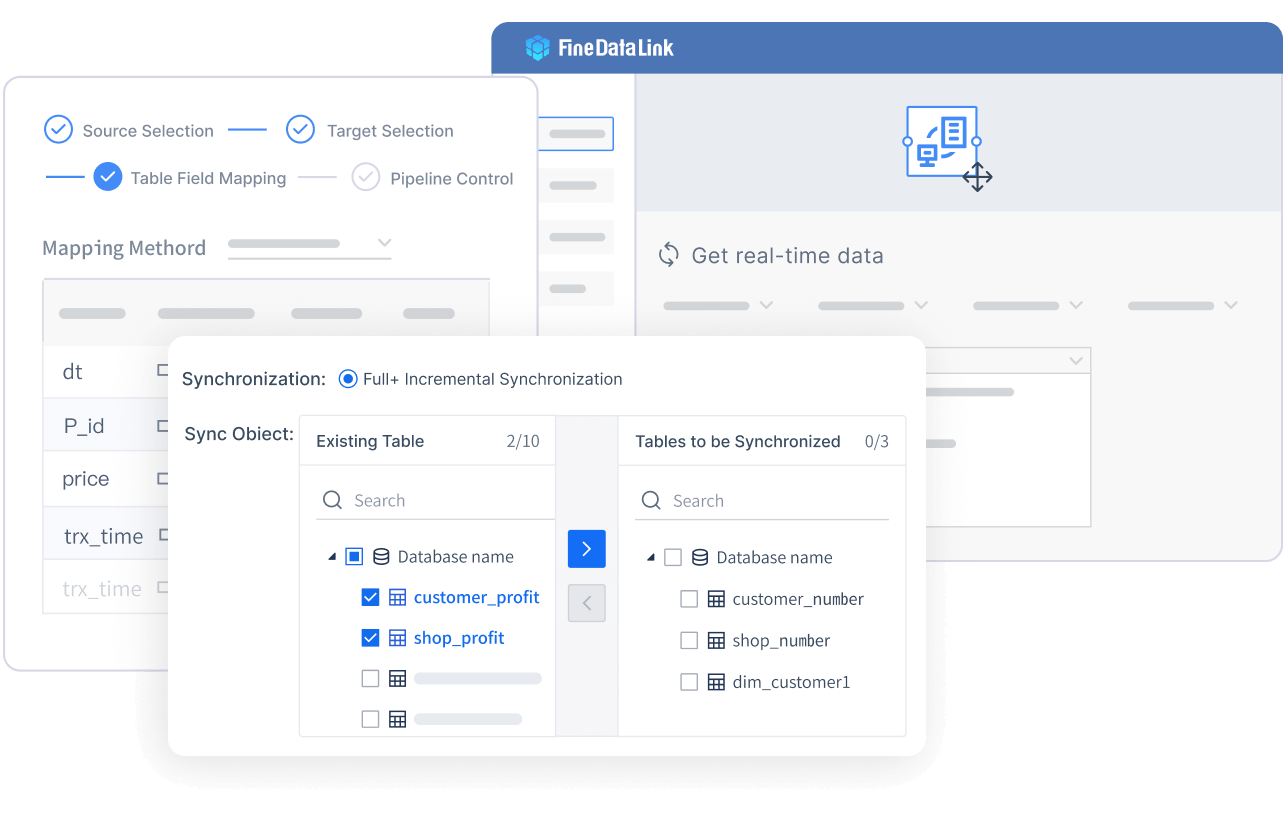
FineDataLink is different from other tools. It gives you both automation and flexibility. Many other platforms only do one thing for data security. FineDataLink puts everything together. You get data integration, monitoring, and help with rules all in one place. This makes your security stronger and easier to handle.
Tip: A platform like FineDataLink lets you see all your data and control who can use it.
You also need tools to watch your data and keep it safe. SIEM tools collect and study security data. They help you find attacks and stop them fast. DLP tools protect your sensitive data from being stolen or lost.
Here are some main things SIEM and DLP tools do:
SIEM tools work well with DLP tools. You get alerts when something is wrong. You can act fast to fix problems before they get worse.
Cloud security is very important for every business now. You store more data in the cloud, so you need strong protection. New solutions help you keep your cloud data safe.
Some top cloud security solutions in 2025 are:
Cloud security tools help you watch your data, find risks, and act fast. You get real-time updates and can protect data in many clouds. FineDataLink works well with cloud security tools. You can connect data from different clouds and keep it safe.
Note: Using platforms and cloud security tools together gives you the best protection. You can manage risks, follow rules, and keep your business working well.
You have many problems when you try to keep your company’s data safe. The table below lists some of the biggest problems:
| Challenge | Description |
|---|---|
| Data Sprawl | Sensitive data is spread across many platforms. This makes it hard to find and protect. |
| Lack of Visibility | Companies have trouble finding and labeling data. This makes it hard to keep data safe. |
| Shadow IT | People use apps without permission. These apps can hide from security and cause leaks. |
| Legacy Systems | Old systems do not have new protections. This makes them easy for attackers to break into. |
| Insider Threats | Workers can make mistakes or share secrets on purpose. This puts data at risk. |
| Disconnected Systems | Security tools that do not work together slow down threat detection. This makes things more complex. |
To fix skill gaps, you should hire skilled people. You should also help your team learn more. Give training and help them get certifications. Let your team practice and get better. You can work with training groups and use government help. FanRuan gives guides and step-by-step videos. These help your team learn FineDataLink and other tools fast.
Tip: Help your team grow with training and simple guides.
Hybrid work brings new dangers. Many workers use different devices and work from many places. You must keep all devices safe and control who gets in. Use Unified Endpoint Management to watch every device. Use Zero Trust Network Access to check users and devices before letting them in. Teach your team safe online habits. Many attacks happen because people make mistakes or use unsafe devices.
FanRuan’s support team can help you set up safe data flows for hybrid work. You get clear steps and quick help with your questions.
You must follow many rules to keep data safe. The table below shows some important laws and standards for 2025:
| Compliance Requirement | Effective Date | Description |
|---|---|---|
| GDPR | Ongoing | Data protection and privacy in the EU. |
| CCPA | Ongoing | Rights for California residents. |
| HIPAA | Ongoing | Health information privacy. |
| PCI DSS | Ongoing | Payment data security. |
| SEC Cybersecurity Disclosure Rules | 2025 | Public companies must report cybersecurity incidents. |
| ISO/IEC 42001 | 2025 | Responsible AI development and deployment. |
| COPPA Revisions | Expected 2025 | Updates for children’s online privacy. |
| Australia Privacy Act Reforms | Late 2025 | New privacy laws like GDPR. |
You should know which rules your business must follow. Sort your sensitive data and use encryption. Limit who can see important data. Make a plan for security problems. FanRuan gives compliance help and updated guides, so you can meet these rules with confidence.
Note: Check your security and compliance steps often. Use FanRuan’s resources to keep up with new laws and threats.
You can keep your business safe by using good data security steps.
Check your security often. FineDataLink by FanRuan helps you handle data safely and follow the rules. Start now to make your data security better.
Enterprise Data Model Explained for 2025
Comparing the Best Enterprise Data Integration Platforms
Enterprise data warehouse explained and why it matters
What You Need to Know About Enterprise Data Protection in 2025

The Author
Howard
Data Management Engineer & Data Research Expert at FanRuan
Related Articles
What is a data management platform in 2025
A data management platform in 2025 centralizes, organizes, and activates business data, enabling smarter decisions and real-time insights across industries.
Howard
Dec 22, 2025

Top 10 Database Management Tools for 2025
See the top 10 database management tools for 2025, comparing features, security, and scalability to help you choose the right solution for your business.
Howard
Dec 17, 2025

Best Data Lake Vendors For Enterprise Needs
Compare top data lake vendors for enterprise needs. See which platforms offer the best scalability, integration, and security for your business.
Howard
Dec 07, 2025